In this article, I present two tools for managing secrets. One is essential. The other is geeky. Both strive for being maximally simple and easy to understand.
This is part #3 in a four-part series on managing my digital life. The series
starts with
part #1 here.
Without further ado: here are pa and psst.

pa: the simplest password safe that I know of
pa is a password safe. It stores passwords in encrypted form on my
computer. It lives at https://github.com/biox/pa/.
Interlude: A password safe is an absolutely essential tool. Many accounts still require passwords. The alternative to a password safe is either impossible (remembering all the passwords) or insecure (using the same password everywhere). Moreover, a safe does more than just storing passwords. It also serves as a directory of all my accounts and assets.
A few features make pa nice to use:
- It is integrated with
git, so that I can sync my passwords between computers, and back them up easily. - It has a text interface with tab-completion.
pa showis the command to retrieve a password. Tab completion means that to get my Amazon password, instead of typing the full commandpa show internet/amazon, I can typepa s in<tab>am<tab>. - It can encrypt passwords for multiple keys (more on this later).
What makes pa stand out is its simplicity. The entire password manager fits in
300 lines of code (about half of these are comments). The code is carefully
written. It is one of the few tools that I depend on, for which I have fully
read and understood the source code.
Not included in the 300 lines is pa’s only dependency: age, the tool
that performs the actual encryption and decryption of passwords. age is a
modern encryption tool that does just that: encrypt and decrypt files. If you
know PGP or GPG, think of age as a successor to these tools, built with 30
years of hindsight and experience. age has an easy-to-use interface, supports
a single, modern set of encryption standards, and avoids most of the pitfalls
that other tools have.
A key feature of the pa and age combination is this: passwords can be
encrypted for multiple keys. The encryption needs only the public part of the
keys. This means I can add passwords without needing access to any of the
secret keys. I keep multiple backups of the password store. This is safe because
encryption protects the passwords from prying eyes. That said, I would recommend
against making the backups public, since the metadata (the list of all my
accounts) is plainly visible.
The secret keys are needed to decrypt and show passwords. In my setup, there
are two secret keys. One is stored on my laptop. The other is a
backup key with a passphrase, intended for situations where I lose my laptop. I
have multiple paper copies of this key, protected using psst.
psst: secret shares made with just pen and paper
psst is a system to make secure paper backups of small secrets. For
example, the passphrase for my age key is an excellent use case for psst.
psst can split a secret into up to four parts, called “shares”. A single share
reveals nothing about the secret. Any two shares can reconstruct it. If I store
the shares in separate places, this system provides high security against
attackers. It also has high availability, because I can reconstruct my secret
even if some of the paper copies are lost.
I made psst to reach new points in the security/availability trade-off. I
wanted to make something that is as simple as possible, where I can understand
every step.
psst is an implementation of
Shamir’s Secret Sharing System.
I chose the parameters in a way that leads to a simple, compact implementation.
Everything fits on one sheet of paper. At the same time, psst is powerful enough
to handle passwords, pass phrases, cryptocurrency seeds and all other types of
small secrets.
All that is needed to use psst is a printer, a pen, and a good six-sided dice.
A user first print out the psst worksheet. Then, they follow the instructions
to encode their secret shares. Finally, the user distributes the shares to
separate locations, and destroys the original secret. By seeing the system
written step-by-step on paper, users can effortlessly understand the math behind
Shamir’s Secret Sharing. It is clear why two shares are necessary to reconstruct
the secret, and a single share doesn’t leak any information.
To see this, go print out a copy of the
psst worksheet.
This is the relevant snippet from the worksheet, showing how a single digit of
the secret is split into shares:
-
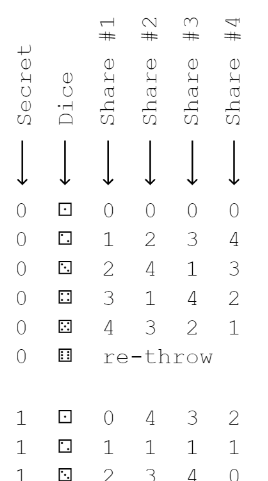
-
When using `psst`, the secret is first encoded as a set of digits from
0to4. Each digit is then split in four shares in a random way, with the help of a dice throw. The snippet shows part of the conversion table: what happens for the digits0and1for each of the six possible dice faces.It is clear that a single share does not reveal the secret: each share can take any value, depending on how the dice falls. Since an attacker does not know what the dice showed, they have no information.
It is also clear how two shares combined can reconstruct the secret. Each combination of two digits appears exactly once, and uniquely identifies the secret digit.
If you are intrigued, I recommend perusing the
psst documentation.
It explains in detail how to use psst, and how I made it. There is an in-depth
discussion of the security and availability trade-off, and also of potential
pitfalls.
Conclusion and outlook
This post presented two tools that can be part of a framework for managing my online stuff. We now have gathered everything needed for a personal key rotation:
- An overview of the accounts and assets that we want to protect (part #1 of this series)
- Decisions for how to protect each asset, to gain adequate security and availability (part #2 of this series)
- The tools we need to achieve that protection (this part)
In the next part, we will finally perform the actual key rotation, and end up with a new set of keys and passwords for a well-protected digital life. Join us on September 1 for part #4 👋🏼