Every few years, I change my passwords, PINs, encryption keys, and make sure that my two-factor authentication is up-to-date and enabled for all important accounts. I call this a personal key rotation. It is a fun exercise and I think of it as a best practice for managing my online identity. That’s why I want to share the knowledge.
In the coming weeks, I aim to publish one post per week explaining the why and how of personal key rotations:
- Gaining an overview of one’s assets (this post)
- What are adequate security and availability? (part #2)
- Tools for managing secrets (part #3)
- Getting your key rotation done (part #4)
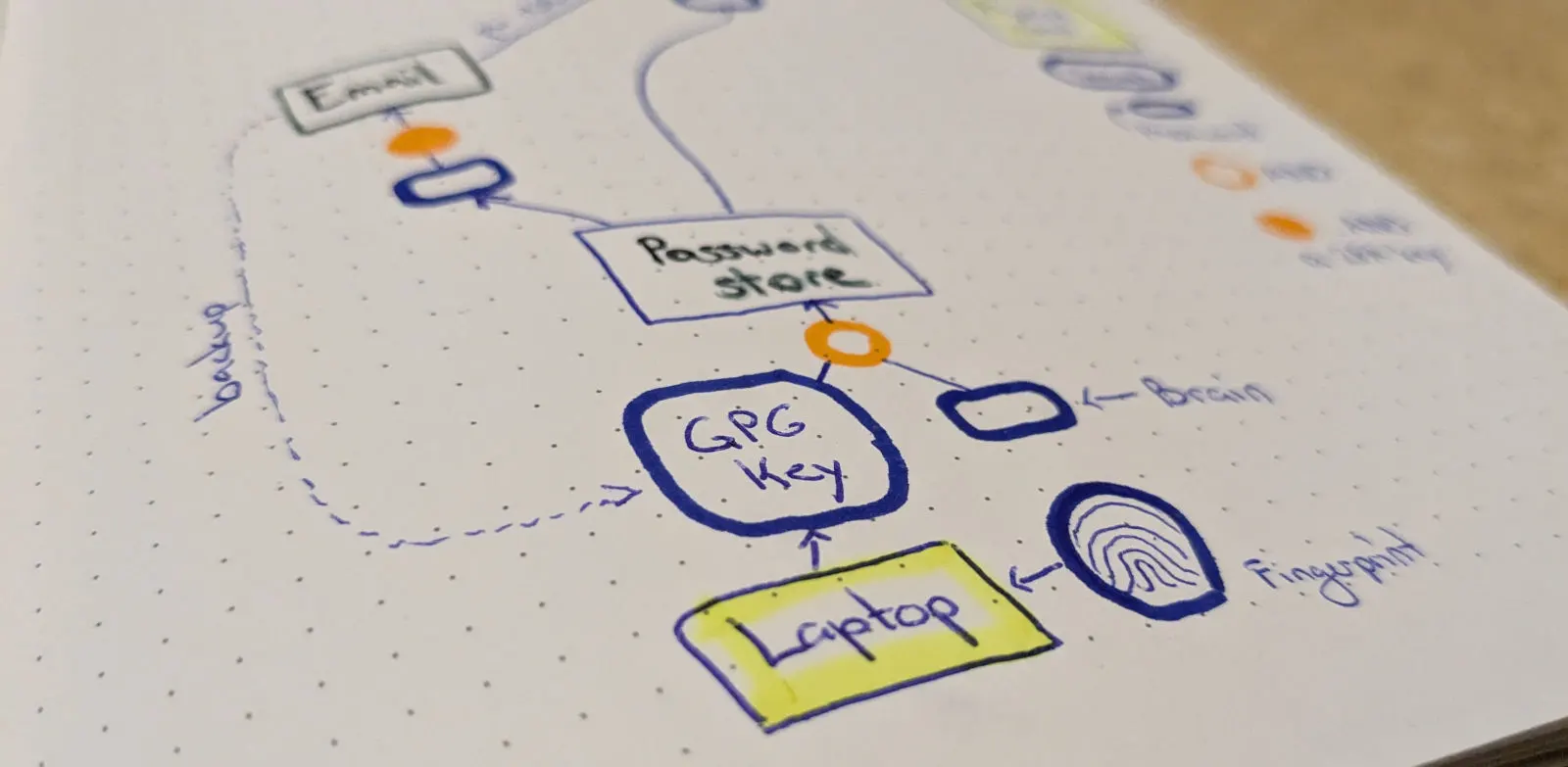
Why do personal key rotations? A key rotation can improve security, for example by removing weak passwords. The main benefit, however, is control over my stuff. This is similar to how a carpenter might do an inventory of her workshop once in a while. It is a way of tidying up and making sure that there is an adequate balance between security and availability. It is a periodic check that I can access the things I own. Losing access is a common problem, arguably more common than theft or getting hacked. For example, some people lose files despite having backups, because the restore process breaks or they’ve lost their backup password.
I will explain more about key rotations, and give step-by-step instructions to do your own, in the future posts in this series. For now, I will focus on the main preparation step: the asset graph.
The asset graph
To prepare for a personal key rotation, it is helpful to get an overview of my online identity and various assets. This includes digital assets like web accounts, app accounts, domain names, and password managers. Also, physical assets like a wallet, a phone, a diary. Secrets are a special type of asset. They give access to something else. I have digital secrets like passwords, PINs, recovery codes; cryptographic secrets like SSH keys and cryptocurrency seeds; physical secrets like house keys, keys for two-factor authentication (2FA), passphrases written on paper, fingerprint-protected passkeys on my laptop, etc.
This post introduces the asset graph, a visual way to list assets and their dependencies. As an internet user, I accumulate many of assets, and they often depend on each other. For example, someone with access to my emails can reset the password for my library account. The asset graph is a way to make sense of this all. If you are like me, making this graph can be quite fun, and give a feeling of tidiness and being organized. Here is an example:
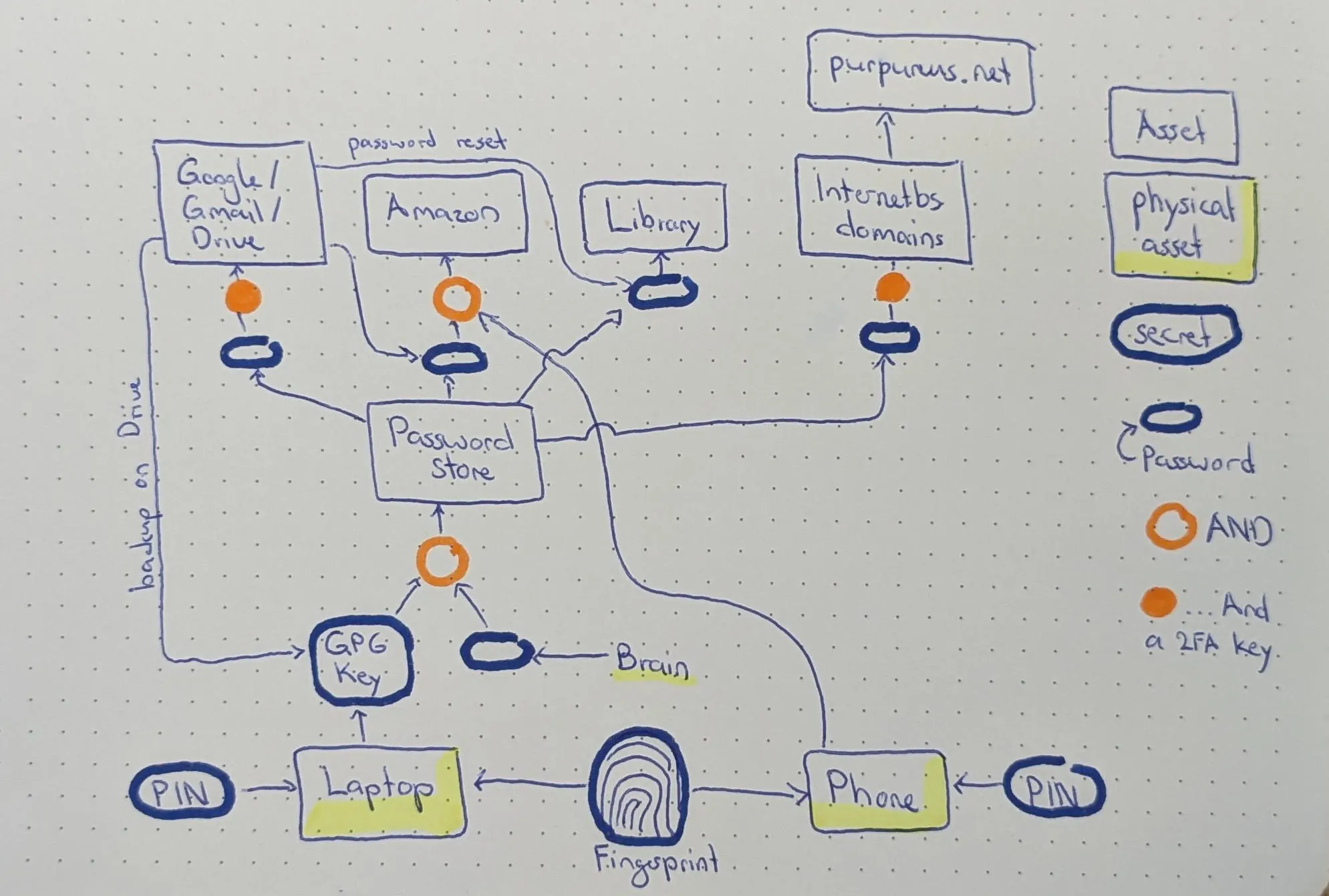
The asset graph has the following structure:
- Each asset is represented by a rectangular node. For example, “email account” and “library account” would both be assets.
- Each secret is represented by a rectangular node with rounded corners. “email account password” and “phone PIN” would be secrets. Passwords are such a common type of secret that I just draw an empty rounded rectangle for them.
- Arrows connect assets that depend on each other. An arrow represents a “has access to” relationship. For example, the email account has access to the library account password (via the password reset mechanism).
- Circles represent
ANDnodes: access is only granted if all incoming arrows are satisfied. For example, my email account might be protected by a passwordANDa 2FA key. Asset nodes are implicitlyORnodes: if they have multiple incoming arrows, any one of them can be used to gain access. For example, both my current password and the password reset mechanism give access to my library account. As a shortcut, circle nodes can omit their default incoming arrow. For example, two-factor authentication is a common protection: I use orange circles with a single incoming arrow to mean “that secret plus any 2FA key”.
How to make your own graph
To create your own asset graph, a good starting point is your password manager. If you don’t have one, look for passwords stored in your web browser or on passwords.google.com. These are your initial secrets. The corresponding accounts are assets. Ideally, you have a nice one-to-one relationship there, because you would never reuse passwords, right ;-) ? The password store itself is an asset with a key or master password. Maybe you have that on a piece of paper in your house, which is protected with a door key… continue expanding outwards in that fashion. Put special emphasis on email accounts that are used to recover other accounts, and on accounts that allow you to sign in elsewhere (e.g., Login with Google).
The graph can be simplified. In my case, I have dozens of accounts that are like my library account: protected with a single password in my password store. It’s probably not worth listing them all, but it is helpful to have at least one representative example of every category.
Note that the asset graph can be quite sensitive. Give yourself enough time and a private room to make it. Consider making an offline pen&paper version.
Outlook: in the next post, we will analyze the asset graph. I will discuss common patterns for accounts. I’ll talk about the right trade-off between availability and security: Availability means how easy we can get to the asset and how unlikely it is that we are locked out. Security means how hard it is for an adversary to gain access.
Further reading
This post draws inspiration from many sources. To learn more, see:
- EFF Surveillance self-defense guide: https://ssd.eff.org/. This guide gives good information about protecting yourself online and how to evaluate threats. It also has articles that are specialized for various audiences, for example students.
- SmartCustody: https://www.smartcustody.com/. A detailed book for protecting high-value assets, with a focus on cryptocurrency.
… and come back next week for the second post in this series :)